CI CD Implementation projects :
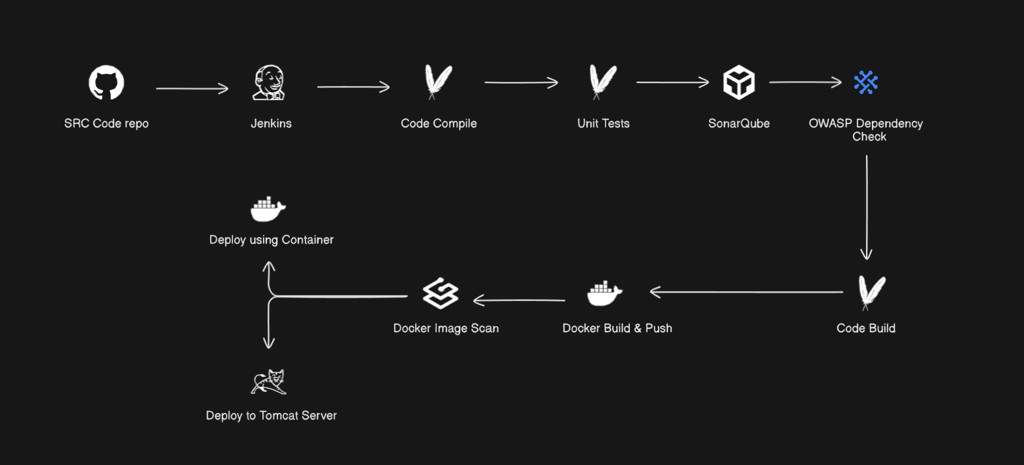
This project focuses on implementing security best practices in a Spring Boot application with two deployment strategies: Docker and Tomcat Server.
GitHub : We have our source code here
Jenkins : our CICD tool, to build and deploy our app. Jenkins will create a local copy of the source code and this copy will be created inside jenkins workspace.
Maven : Code Compile : in this process it will figure out if there are any syntactical or syntax based errors in the code.:
: Unit tests : to see if all our written test cases are working fine or not.
: Code Build : to generate the artifact - a Jar file
SonarQube : a security tool which checks for code quality and finding if there are any vulnerabilities, code smell, technical debts or any such issues. Based on this a report will be generated which is inside sonarqube
OWASP Dependency check : it scans source code and makes a report if there are any known vulnerabilities, categorizes issues in severity based format.
Docker : Building a docker file and pushing it into Docker Hub Repo.
Aqua trivy : Scans docker image for issues or vulnerability.
Later 2 ways of Deployment : Docker and Tomcat.
DevSecOps Project: Secure Deployment of a Spring Boot App
End-to-End CICD Pipeline
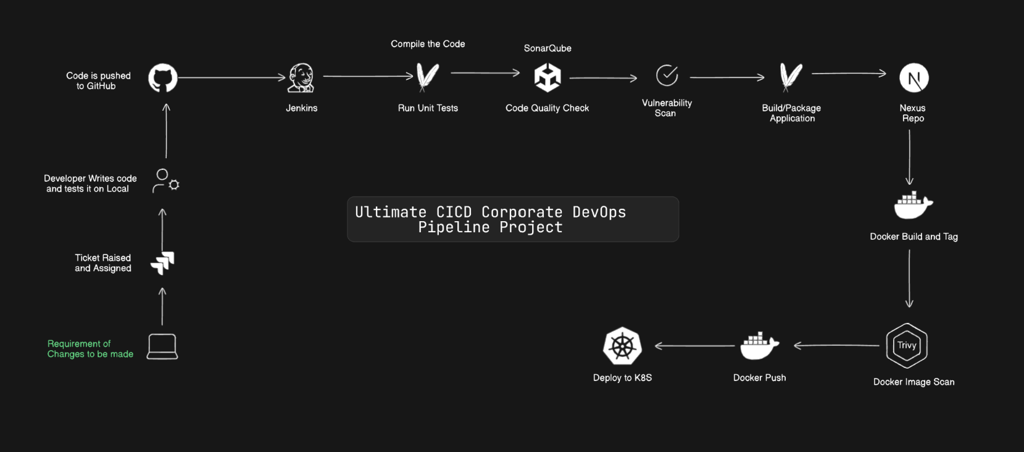
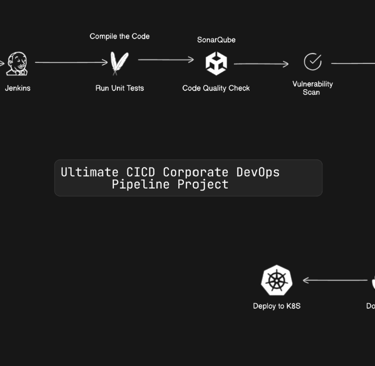
In a corporate DevOps setup, client-requested changes start with a Jira ticket. Developers update the code in Git, triggering a CI/CD pipeline that builds, tests, and creates deployable artifacts. After approval, the change is verified in staging and deployed to production using automation tools like Terraform or Kubernetes. This process ensures smooth, efficient, and error-free deployments.
The following project demonstrates how this workflow is implemented in a real-world scenario.
We start by making servers : Jenkins (Master/Worker) , SonarQube, Nexus & Kubernetes (one Master, 2 Workers)